QinQ tagging
Taking a look at QinQ technologies. Had to work with a cloud provider that leveraged this technology and wanted to take a look at what the heck QinQ was under the hood. After labing this one up there isn’t much to it and it reminds me of “VLAN hopping”, an old security issue I remember reading up on during my Certified Ethical Hacker studies years ago.
Topology
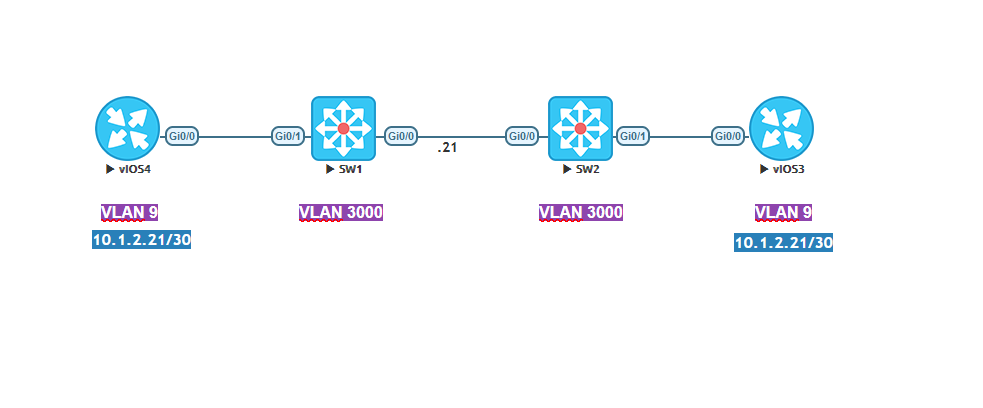
…show me the config
SW1
conf t
!
vlan 3000
name customer XYZ
!
int g0/1
switch access vlan 3000
switch mode dot1q-tunnelSW2
conf t
!
vlan 3000
name customer XYZ
!
int g0/1
switch access vlan 3000
switch mode dot1q-tunnelR1
conf t
!
vlan 3000
name customer XYZ
!
int g0/1
switch access vlan 3000
switch mode dot1q-tunnelR2
conf t
!
vlan 3000
name customer XYZ
!
int g0/1
switch access vlan 3000
switch mode dot1q-tunnel
0 Comments